OpenID Connect
It is possible to switch the Planon SDK to OpenID Connect (OIDC) authentication in the Environment management gadget.
This will currently break the Planon AutoCAD Plugin implementation, so if the Planon AutoCAD Plugin integration is used, do not switch your enviroment to OIDC authentication. This will be fixed in a newer version of Planon so that the Planon AutoCAD Plugin will support OpenID Connect in the near future. |
The default behavior of the SDK is unchanged, this means if no additional configuration is done, form authentication and Planon access key is present.
Enabling OpenID connect disables form authentication. Planon Access key is optional supported in combination with OIDC, or Planon Access Key only. For more information, see the following table:
Form Authentication | Planon Access Key | OpenID Connect | |
|---|---|---|---|
Option 1 (default) | Enabled | Enabled | Disabled |
Option 2 | Disabled | Enabled | Enabled |
Option 3 | Disabled | Disabled | Enabled |
Option 4 | Disabled | Enabled | Disabled |
Installation
Planon Cloud configuration
1. Enable OpenID Connect authentication for SDK in the Environment Management gadget.
In order to see this option, your environment must be running on the latest Cloud platform and SSO must be enabled. |
2. In Keycloak, create a client with a self chosen client name (in the following image: sdk-example1. The root URL should be equal to the SDK interface URL.
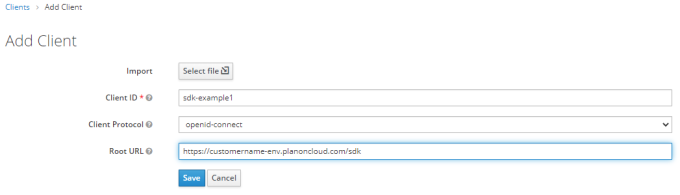
3. In the next screen, configure the client to meet up to your security policies and save the changes.
• Both Client credentials as well as Authorization code flow are supported. • When using Client credentials flow make sure that Service account is enabled. |
4. In Planon make sure a user is present that can be used by the configured client above. When Client Credentials flow is used, a service account user for the client must be present in Planon.
Example
If the client name is sdk-example1, than a user with the account name service-account-sdk-example1 must be present and active in the Planon application.
Usage
To get access to the SDK service via OpenID Connect, take the following steps:
1. Retrieve an access token at the keycloak service via the Client created in the installation step.
2. Send this token as Bearer token to the Planon SDK service.
Troubleshooting
The following table lists a few common errors.
Error | Description |
|---|---|
401 Unauthorized | Either no access token or an expired access token has been sent to the Planon application. |
500 Internal error | The user account does not exist in the Planon application. |
WebDAV
When enabling OpenID connect for WebDAV, in addition to the configuration mentioned in this article, you must also assign product definitions to the proper user groups.
When using Basic authentication, you can log on to the various WebDAV locations by using your environment's credentials.
After enabling OpenID connect for WebDAV, these credentials will no longer work. Instead, please assign the various product definitions for WebDAV to the relevant user groups.
The following WebDAV product definitions will be available:
• WebDAV
• WebDAV_Audit
• WebDAV_Backup
• WebDAV_PEET
• WebDAV_TMS
• WebDAV_Webservices
These product definitions will enable you to determine/authorize access to the various WebDAV locations.
Please note that assigning a WebDAV product definition to a user group is explicit. Without assigning WebDAV product definitions, no user can access WebDAV locations! See also: Arranging access to Planon products and subsequent articles. |
Mobile
The Planon Live app will use offline tokens when OIDC has been enabled. The advantage of using offline tokens is that users need to authenticate a lot less.
Default behavior is that after initial log in, a user can use the app without further authentication once per 30 days. If the user uses the app at least once per 29 days he/she can use the app without re-authentication for maximum 180 days (from the initial log in).
If an administrator wants to change the default timings, this is configured in the Identity Broker environment under Clients / PlanonMobile / Advanced Settings.
• Client Offline Session Idle = 30 days (default)
• Client Offline Session Max = 180 days (default)
Please make sure the Offline Session times are always longer than 1 hour!! If set to a shorter timing unexpected behavior will occur. |