Overview
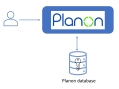
When a Cloud environment is delivered, the following way of authentication is the default configuration.
This configuration is also the default on-premise configuration; it uses form authentication for the Planon environment. |
Keycloak
Enabling Single Sign On (SSO) on a Cloud environment introduces Keycloak authentication. Keycloak can be configured to use different authentication sources.
January 1, 2025
On January 1, 2025, Planon User federation will be implemented. Please note that this is release independent (from L92 onwards). By default this automatically applies to newly configured SSO environments.
• Planon User federation applies to new and existing customers.
◦ For existing customers who have configured SSO (in the past), nothing will change.
◦ For existing customers who have not yet configured SSO, this will apply.
◦ For new customers, this automatically applies.
• What it means:
If a customer is using a Planon environment (L92 or later) and enables SSO (Keycloak) after January 1, 2025, the current user passwords will remain working via the Planon User provider in Keycloak.
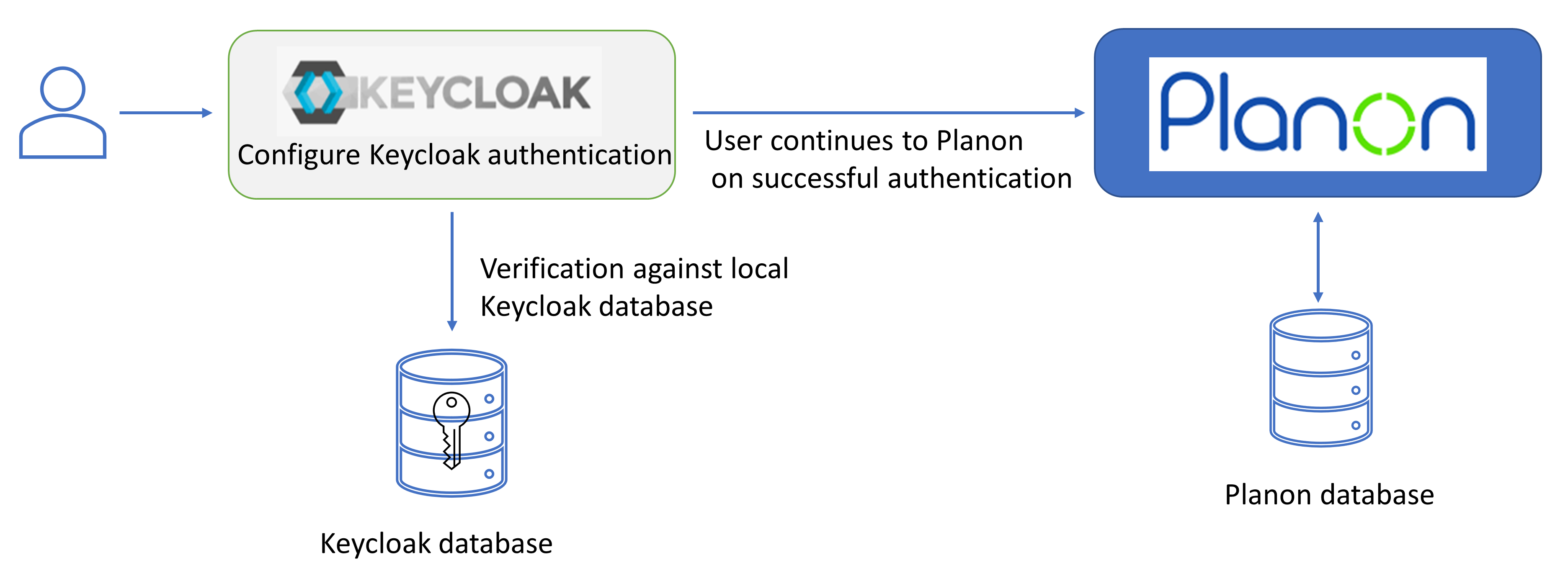
Keycloak authentication
By default, the authentication via Keycloak is configured as follows.
This configuration needs to be adjusted by the customer according to the customer's specific (security) requirements. The default configuration already contains all existing users that are able to log in to Planon. |
The following diagram shows the possible configuration options for authenticating users.
This includes the configuration that needs to be applied by the customer.
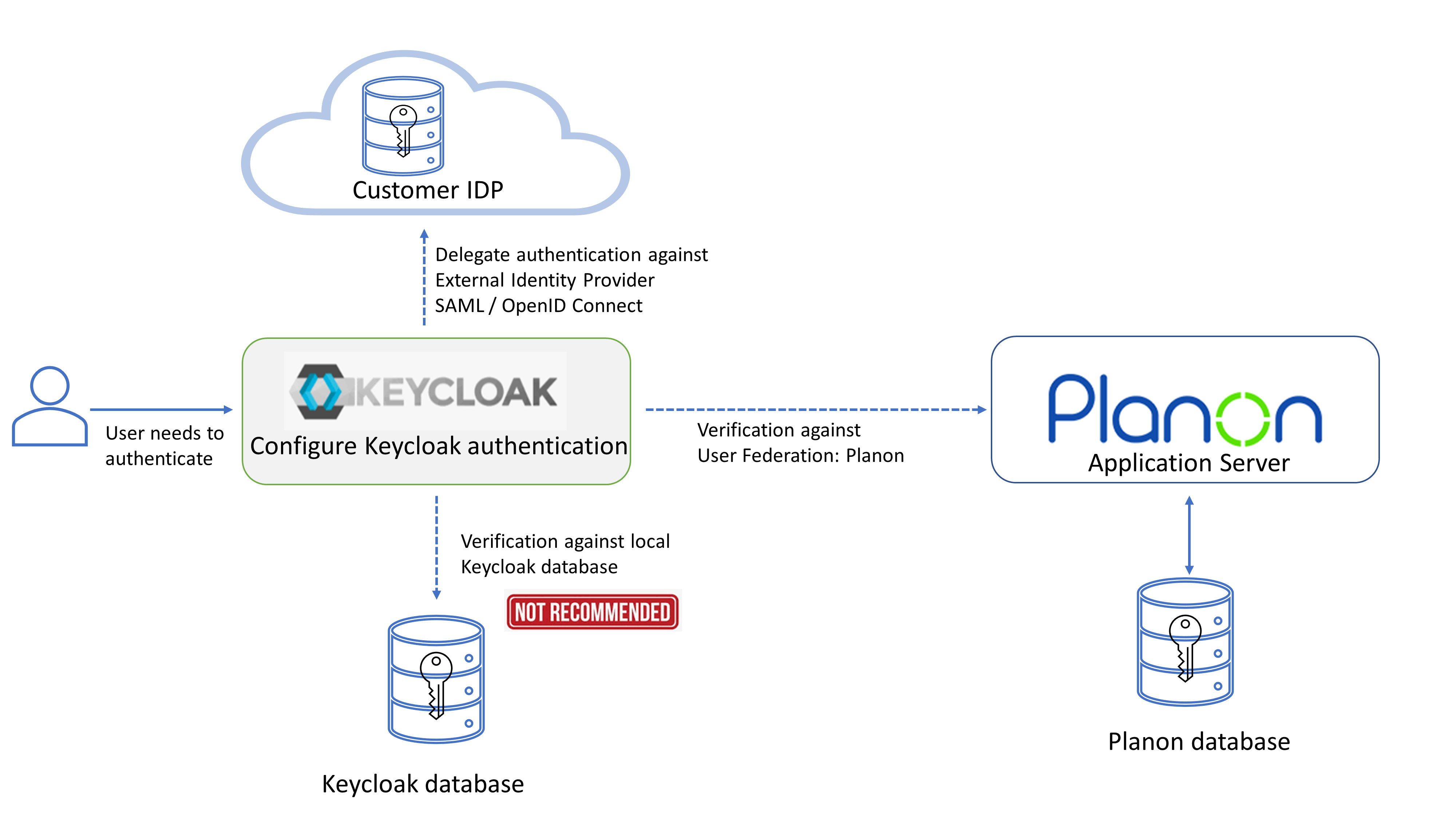
Customer's options
The customer can choose to:
• Add accounts to the Keycloak database for users to authenticate against Keycloak.
CAUTION | This is not recommended! |
• Add Planon provider in Keycloak under User federation.
This way, users authenticate against the account in Planon database via Keycloak
• Add a external IDP under Identity Providers in Keycloak.
This way, users authenticate against the external IDP of the customers choice via Keycloak.
Notice | This is the recommended solution. |