Privacy sandbox compatibility
To enhance security and streamline authentication management, Planon introduced a single-domain approach for its OpenID Connect Single Sign-On solution. This feature Privacy sandbox compatibility is available from L87.
• For environments enabling SSO the very first time, this feature is by default enabled.
• For existing customers already using SSO, additional configuration is required before this option can be enabled.
Prerequisites
The configuration of the Identity Provider (IDP) needs to be modified before you can enable this setting.
Kindly request your IT organization to expand the current SSO configuration (configuration of your external Identity Provider (IDP)) for your Planon environment.
Request to add two additional redirect URLs alongside the existing allowed redirect URL.
• The first URL should be identical to the existing URL, but without the "-sso" part in the hostname.
• The second URL should be customized to match your custom domain (if no custom domain is configured, only the first additional URL is needed).
Example
Current redirect URL in the IDP configuration:
https://customerenvironment-prod-sso.planoncloud.com/auth/realms/planon/
First redirect URL to be added:
https://customerenvironment-prod.planoncloud.com/auth/realms/planon/
Optional, when a custom domain is configured (custom domain used in this example is facilities.customer.com):
https://facilities.customer.com/auth/realms/planon/
After the IT department confirmed the requested change, you can proceed. |
Configuration
1. Enable the setting in the Environment Management gadget > SSO tab under the Privacy sandbox compatibility option by clicking the OFF button.
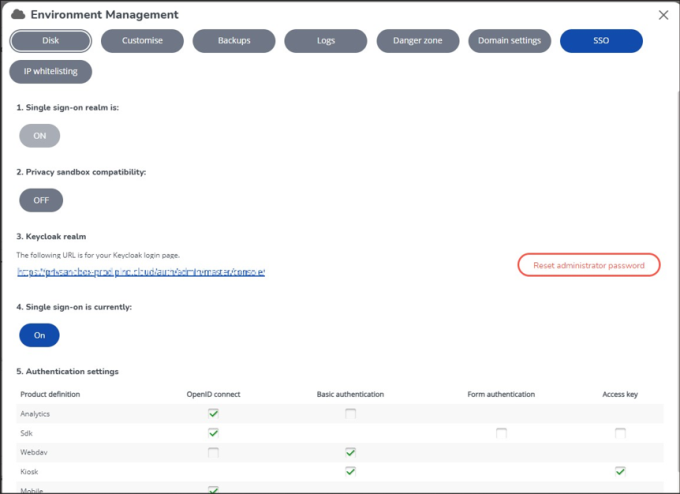
2. A pop-up will appear. Click Restart Instance’ to restart the environment.
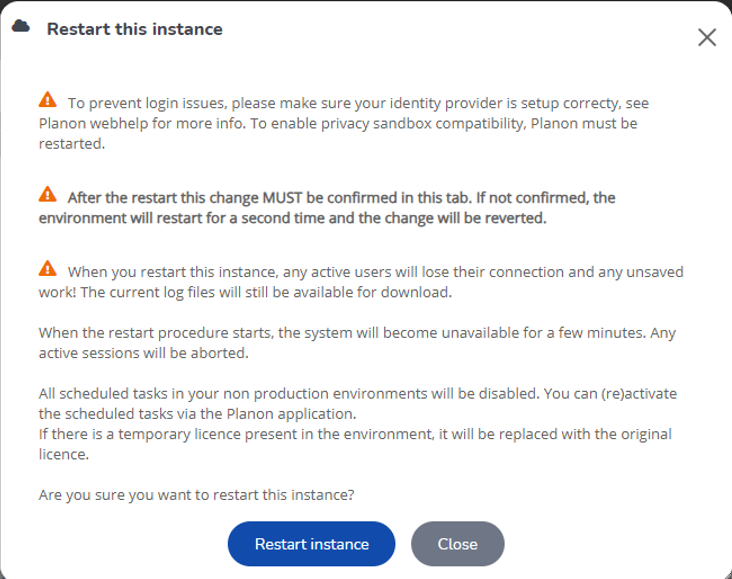
It is crucial that you log on to the Planon application and access the Environment Management Gadget within 10 minutes after the environment restarts. Always Log on to your environment via Single Sign On (not as supervisor). |
On the SSO tab, please verify that the change has been successfully implemented. If the confirmation is not confirmed within 10 minutes after the environment has restarted, the environment will restart for a second time and the change will be reverted. This step is essential to prevent any configuration errors resulting in making the Planon Cloud environment unusable.
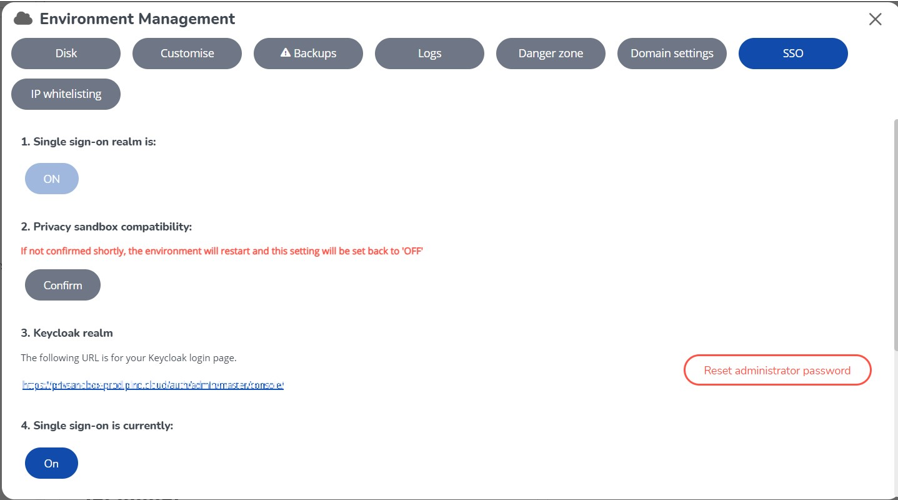
After confirmation, please be aware that the option will be permanently enabled and cannot be disabled. Note: the improved feature Activate Privacy Sandbox will automatically be enabled when Privacy Sandbox Compatibility is confirmed. |
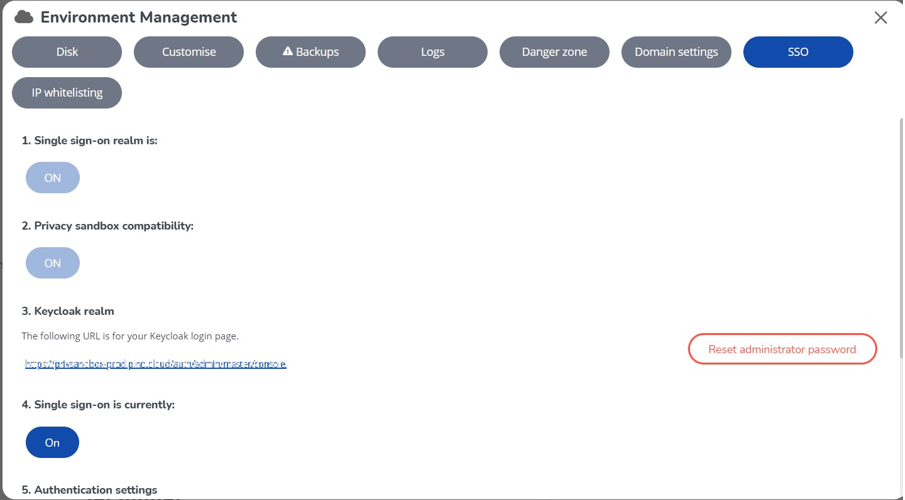
4. If a logoff URL is set for the environment, ensure it is updated to reflect the changes made.
If a custom domain is not used, remove the "-sso" part from the URL.
If a custom domain is configured, adjust the hostname to match the custom domain.
By following these steps, your Planon Cloud environment is future-proofed for the phasing out of third-party cookies.